SOC-as-a-Service with Zero Trust-as-a-Service
Security Operations Center
THE SITUATION UNDER CONTROL
Building a security operations center (SOC) can take several years.
We offer you a unique service: Security Operations as a service on request with Zero Trust as a service!
What does that mean for you?
- 24/7 incident response
- Certified, tested and experienced security analysts
- Incident response teams and root cause analysis
- Reveal AI™, our internal AI threat intelligence platform
- Every manually evaluated alarm improves EventFLow for all customers
- Custom recommendations to improve security
And it’s that simple: Your firewall and other security systems forward their events to our systems for analysis in a highly secure manner.
This means you can easily get your security operations center without a lot of personal investment, without looking for personnel and without expensive systems.
Let us advise you, we would be happy to show you more!
Zero Trust as a service
We’ll help you introduce Zero Trust Security!
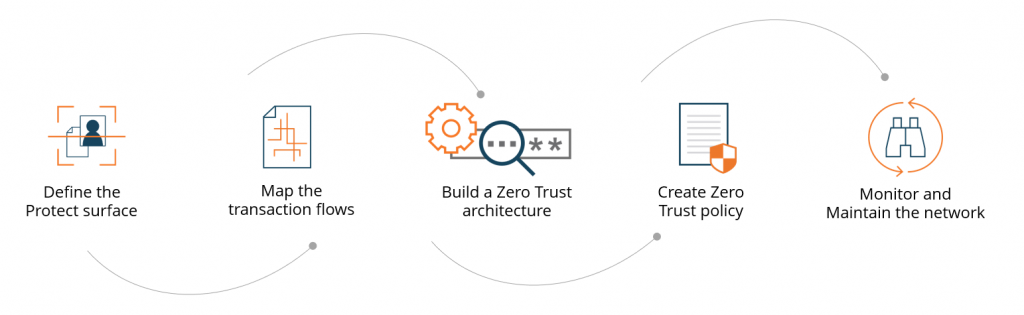
Our service supports you in a simple and clear manner in taking the five steps to introducing Zero Trust:
- Define protection areas
- Mapping data flows
- Zero Trust – Building Architecture
- Zero Trust – Create policies
- Monitor, Maintain, Improve
Step 1: Define protection areas
In the first step, the protection areas are defined. For this purpose, the assets are recorded, classified and protection requirements assigned.
This is presented very clearly in our Zero Trust SOC-as-a-Service.
Step 2: MAP DATA FLOWS
In the second step, the data flows are automatically mapped from the existing data.
The corresponding overview in the Zero Trust Fitness area clearly shows which data flows where.
This means you can see at a glance which network areas are communicating with which and you can quickly see where data flows need to be restricted.
Step 3 & 4: BUILD ZERO TRUST ARCHITECTURE AND CREATE GUIDELINES
Our platform also supports you with these two steps.
The necessary adjustments can be quickly derived from steps 1 and 2 and implemented here.
Step 5: Monitor, Maintain, Improve
Monitoring your infrastructure and Zero Trust Fitness provides an exceptional overview of the security situation.
Constant improvement ensures you a consistently high level of security with little effort.
